Building a Secure Foundation: Integrating Security by Design into Your CI/CD Pipeline
In today's rapidly evolving technological landscape, the integration of security measures has become more critical than ever before. With the advent of continuous integration and continuous delivery (CI/CD) pipelines, software development teams are under immense pressure to deliver features at unprecedented speeds. However, amidst this rapid pace, security often takes a backseat, leaving applications vulnerable to various threats and vulnerabilities.
Integrating Security by Design principles into your CI/CD pipeline is now more crucial than ever before. By embedding security considerations at every phase of the software development lifecycle, organizations can proactively identify and mitigate risks, ensuring the integrity and security of their applications.
Introduction
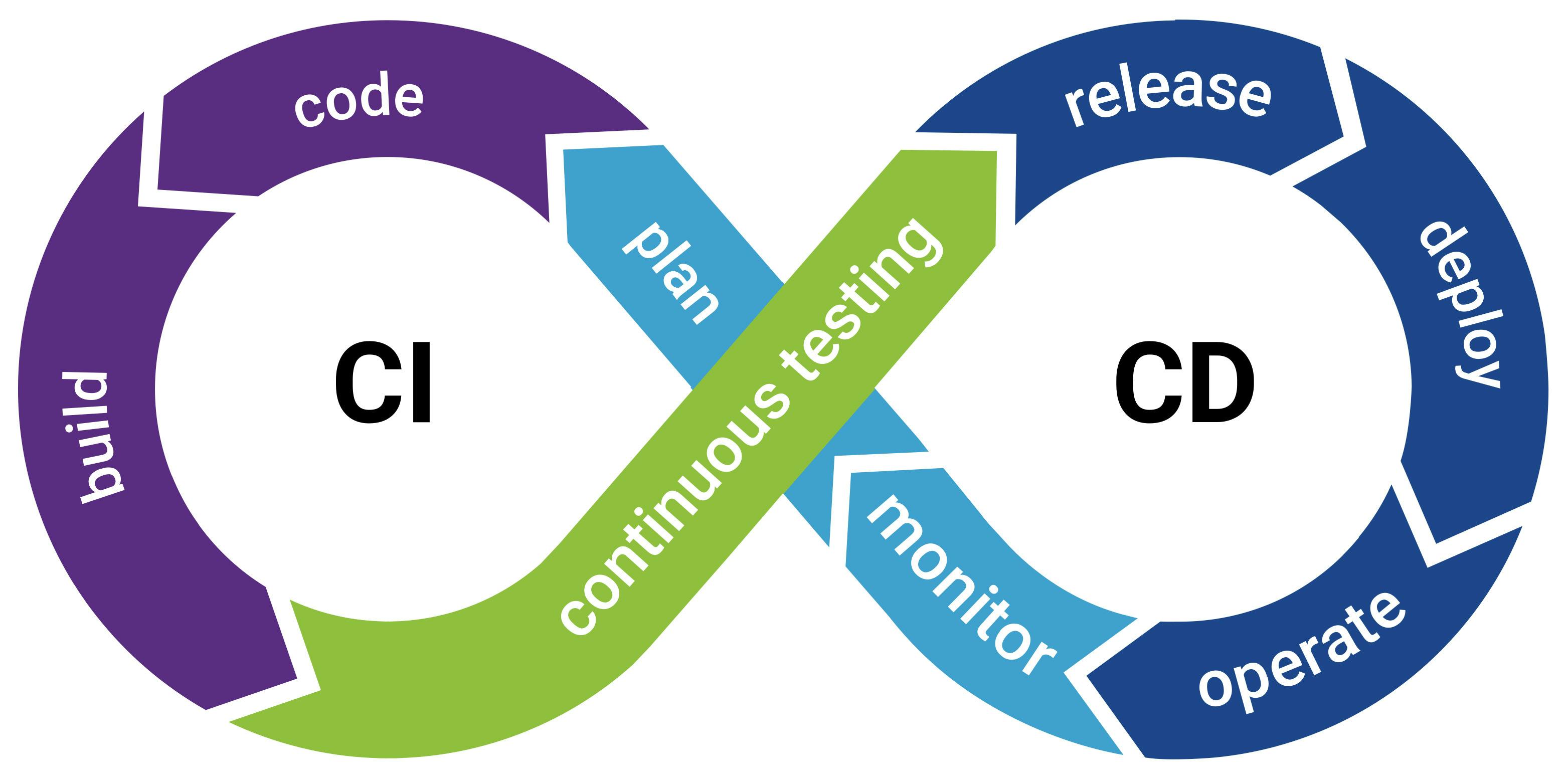
The software development lifecycle has undergone a significant transformation with the widespread adoption of CI/CD pipelines. Continuous Integration (CI) is a development practice where code changes are frequently integrated into a shared repository. It involves automated build and testing processes to ensure code quality and detect bugs early in the development cycle.
Continuous Delivery (CD) extends CI by automating the process of deploying code changes to production-like environments for testing, validation, and potential release. CD focuses on ensuring that code changes are always in a deployable state.
Continuous Deployment (also CD) takes CD a step further by automatically deploying code changes to production environments after passing all tests and validations. This approach reduces manual intervention and accelerates the delivery of new features and fixes to end-users. These pipelines enable developers to automate the process of building, testing, and deploying code, resulting in faster delivery cycles and increased agility. However, as organizations strive to keep up with the demands of rapid development, security often becomes an afterthought. This approach leaves applications vulnerable to many threats, including data breaches, malware attacks, and unauthorized access.
Understanding Security by Design:
Security by design is a software and hardware development approach focused on minimizing vulnerabilities and preventing attacks through continuous testing, authentication measures, and adherence to best programming practices. Unlike the common practice of addressing security issues after development, this approach integrates security from the outset, recognizing that patching vulnerabilities retroactively is less effective. Particularly vital in the expanding Internet of Things (IoT) landscape, where nearly any device can be networked, security by design addresses challenges posed by traditionally non-networked appliances. This model contrasts with less robust methods such as security through obscurity, minority, and obsolescence.
Security by design is crucial in software development despite perceptions that it hinders production and incurs costs. Integrating security into the Software Development Life Cycle (SDLC) fosters a continuous security workflow and reduces user friction. This approach addresses organizational challenges such as cybersecurity talent shortages and changing regulatory environments like GDPR. It also aligns with the principles of continuous delivery/integration (CI/CD), which are common in modern organizations.
Benefits of Security by Design
Benefits of the Security by Design approach include preventing vulnerabilities, future-proofing systems against evolving threats, enhancing data protection, promoting transparency and collaboration, implementing internal solutions for better defense, and empowering employees with the tools and knowledge to stay safe online. While there may be upfront costs, the long-term benefits include a more streamlined security posture, increased customer trust, and avoidance of costly breaches. Starting the implementation early in the project development lifecycle maximizes the value gained from this approach.
Real-world success stories demonstrate the effectiveness of security by design in reducing risk and improving overall security posture. Organizations can build trust in technology by prioritizing security from the start and ensuring that customers receive inherently secure products. Ultimately, security by design is not a luxury but a necessity in today's digital landscape.
Companies across various sectors have achieved significant success with secure-by-design outcomes. A leading building supply company slashed costs and time to market for security requirements by 30% while simultaneously fostering increased collaboration between security and development teams. In the banking sector, a large bank significantly reduced risk, improved visibility, and cut the time to assess risk by over 90%, enhancing overall security measures. Similarly, a Smart Home Products brand successfully embedded a Security Champion in every development team, bolstering security across their product lines.
In the realm of consulting, a global consultancy streamlined its threat modeling process, reducing the time required from over 230 hours to just 60 hours, marking a substantial efficiency improvement. Moreover, several federal government organizations achieved remarkable efficiency enhancements by reducing their time for compliance activities from months to mere days, ensuring timely adherence to regulatory standards. These success stories underscore the tangible benefits of adopting a secure-by-design approach, ranging from cost savings to improved risk management and compliance efficiency.
Integrating Security into CI/CD Pipelines:
Integrating robust security measures into your pipeline is not just important; it's essential for safeguarding your organization's assets and maintaining trust with stakeholders. Firstly, protecting your code from potential attacks is paramount as it is a critical asset vulnerable to various malicious entities seeking to exploit weaknesses. Additionally, preventing data breaches is imperative, given that any compromise within your pipeline could result in the unauthorized exposure of sensitive information, leading to significant consequences for your organization, including legal and financial ramifications.
Moreover, adhering to regulatory requirements and industry standards is crucial for maintaining trust and credibility. Ensuring compliance with policies helps mitigate risks and demonstrates your commitment to upholding the highest standards of security and privacy. By integrating security measures seamlessly into your CI/CD pipelines, you enhance the overall security posture and streamline the development process, enabling faster and more efficient software delivery.
Furthermore, embedding security practices into every stage of the pipeline is fundamental for implementing a security-by-design approach. Automated security testing tools are pivotal in identifying and remedying vulnerabilities throughout the development lifecycle. By conducting security checks at each phase, developers can ensure that only code meeting predefined security criteria advances further, thus minimizing the risk of introducing vulnerabilities into the final product.
In essence, a secure pipeline protects your organization's assets and reputation and contributes to delivering high-quality code that is resilient to cyber threats. By prioritizing security throughout development, you bolster software integrity and reliability and instill confidence in your products among users and stakeholders.
Pipeline Security Best Practices:
Implementing robust security practices within CI/CD pipelines is essential for safeguarding software integrity and protecting against potential threats. Key principles include integrating security considerations into software requirements, enforcing secure code guidelines, utilizing appropriate security tools, and conducting regular audits and vulnerability testing. Additionally, addressing potential abuse cases and ensuring the trustworthiness of reused software are crucial steps in mitigating risks effectively. Continuous feedback on security effectiveness and educating development teams on secure coding techniques further enhance software security posture.
Moreover, threat modeling is critical in identifying hidden security risks and prioritizing vulnerabilities. By focusing on the most relevant threats, development teams can allocate resources efficiently to mitigate potential risks.
Strong authentication and authorization mechanisms are paramount to regulating access effectively regarding CI/CD resource security. Throughout the pipeline, encryption of sensitive data, such as credentials and configuration files, ensures protection against unauthorized access. Regular updates of dependencies and libraries are vital to address known security vulnerabilities and maintain system integrity. Leveraging containerization and orchestration technologies provides isolation and security for application components, bolstering resilience against potential threats.
Furthermore, adopting infrastructure-as-code principles facilitates consistent management of security configurations across different environments. This approach streamlines management processes and ensures that robust security measures are consistently enforced throughout the software development lifecycle. By adhering to these best practices, organizations can enhance their overall security posture and minimize the risk of exploitation by malicious actors.
Measuring Security Performance:
DevSecOps metrics and measurements are pivotal in evaluating the efficacy of Security by Design initiatives within CI/CD pipelines. One pivotal metric is the application change time, delineating the duration from the moment code is committed to its deployment in the production environment. This metric, essentially, serves as a litmus test for the velocity of the development pipeline, providing insights into its swiftness and agility.
Complementing this is the application deployment frequency, which quantifies the number of deployments to the production environment within a specified timeframe. When analyzed in tandem with others, this metric offers a comprehensive view of deployment patterns and their adherence to established timelines.
When it comes to operational stability, availability emerges as a critical metric, encapsulating an application's uptime or downtime over a given period. Its significance lies in ensuring adherence to Service Level Agreements (SLAs) and maintaining seamless service delivery.
Meanwhile, the change failure rate stands as a sentinel, indicating the percentage of failed production deployments. Its scrutiny reveals potential skills, processes, or infrastructure deficiencies, necessitating corrective action to bolster deployment reliability. Change volume steps forward to quantify the influx of new features or functions deployed over time, serving as a barometer for development velocity and project progression.
On the support front, issue resolution time measures the average duration taken to address reported issues. This metric underscores the promptness for identifying and rectifying defects, which is crucial for maintaining a robust user experience.
Issue volume enters the fray, visually representing customer-reported issues within a specified timeframe. This metric offers insights into customer satisfaction levels and the magnitude of development challenges faced. Transitioning to operational resilience, Mean Time to Recovery (MTTR) assumes significance. It spotlights the duration between a failed deployment and the complete restoration of production operations. It serves as a gauge of operational efficiency and the organization's ability to swiftly rectify disruptions. Security prowess is expressed in the time to patch metric, which quantifies the duration between the identification of a vulnerability and the deployment of a patch. This metric underscores the organization's agility in addressing security vulnerabilities promptly, thus fortifying its defenses.
Lastly, time to value emerges as a metric tailored to specific business objectives. It tracks the duration between a feature request and the realization of tangible business value. This metric aligns development efforts with overarching business goals, ensuring a streamlined and purposeful development process.
Conclusion:
In today's rapidly evolving technological landscape, the integration of security measures has become more critical than ever before. With the advent of continuous integration and continuous delivery (CI/CD) pipelines, software development teams face unprecedented pressure to deliver features at exceptional speeds. However, amidst this rapid pace, security often takes a backseat, leaving applications vulnerable to various threats and vulnerabilities.
Integrating Security by Design principles into your CI/CD pipeline is now more crucial than ever before. By embedding security considerations at every phase of the software development lifecycle, organizations can proactively identify and mitigate risks, ensuring the integrity and security of their applications.
The adoption of Security by Design strengthens the resilience of software systems and fosters a culture of security consciousness within organizations. By prioritizing security from the outset, organizations can minimize the likelihood of security breaches and mitigate potential damages to their reputation and bottom line.
Furthermore, seamlessly integrating security practices into CI/CD pipelines enhances the development process's efficiency and effectiveness. Automated security testing tools, robust authentication mechanisms, and regular updates of dependencies are just a few examples of the measures that can be implemented to bolster security within the pipeline.
Moreover, measuring security performance through DevSecOps metrics and measurements provides valuable insights into the effectiveness of security initiatives. By tracking key performance indicators such as application change time, deployment frequency, and time to patch, organizations can gauge their security posture and identify areas for improvement.
In essence, organizations can build a secure foundation for their software applications by embracing Security by Design principles and integrating security practices into CI/CD pipelines. In doing so, they protect their assets and maintain trust with stakeholders and demonstrate their commitment to upholding the highest standards of security and privacy in today's digital age.